Remember when almost half the country had all the information needed for any kind of loan stolen? Pepperidge Farm Remembers.
Discord: https://discord.gg/mBPbWcVRYR
Show website: https://whattheshellpod.com
Patreon: https://patreon.com/whattheshell
Intro
Imagine you're a master thief and you've set your eyes on the score of a lifetime. You've spent months and months and months staking out the bank that you've determined you're going to rob. The bank? Well let's say in this little hypothetical that it's one of the countries top financial institutions so you're setting your expectations accordingly. Surely, they've got things locked down, monitored, and tighter than you can possibly imagine.
So we're getting closer and closer to the day of the operation, and as it approaches the unthinkable happens. The master key that you've carefully crafted to get through the first layer of security has leaked to the world. The bank knows about it and now you part of your plan is out in the open even if they don't directly know what could happen.
But you take the risk, the night of your big heist you insert the key and voila. It works. You're in. On to the next step and then the next. As you're walking through this behemoth of an institution it's becoming clear…this place really is NOT that secure. You don't know what they were thinking but this has been a walk in the park. So you make your way in, scope it out, and your mission is complete.
What if I told you something not all to disimilar happened in the late 2010s? It was still a financial institution but the heist we're talking about was not a physical one, and instead of a vault of cash we have the most important details American citizens.
I'm John Kordis, and this episode I'm going to take you back to 2017. We're going down to Atlanta, Georgia and we're going to walk right into Equifax HQ so we can learn about a cacophony of problems let hackers walk almost straight into the data that was supposed to be safeguarded with the best protections out there. This week, we're going to talk about what the shell happened at equifax and why it changed the cyber landscape as we know it.
Set the stage for 2017
There's a lot of moving pieces to this hack, so I want to start by just setting the stage and dipping our toes in the water. I'm taking you back to March of 2017. If you're a movie buff like me, then you've probably seen Logan, Get Out, or Kong Skull Island. We were over a year away from any kind of Infinity War happening. If you're in the US then we're about two months into the Presidency of Donald Trump. For me? I was starting to consider a very important question; When should I start thinking about trying to buy a house? And no, that's not a humble brag or anything like that, it was a major life choice and I wanted to make sure it came with the right amount of forethought, and little would I know but by the time the month was over, it would be entirely possible that the dream of ownership could be gone.
For any of our younger listeners, I'll give you the cliff notes on a home loan. To get a loan like that you need a couple things. Capital, the money for a down payment, proof of income / work, you know the ability to say I can keep making payments, and a good credit history, the report that says "Yeah, you can trust me. I've been making these payments on time for quite a while". Don't get me started on that bit because if you're a renter you'd think that would count but more often than not it doesn't.
Anyways, in the US there are three major agencies monitoring the credit of the United States citizens; Experian, TransUnion, and Equifax. For this episode we'll be focusing on that last one, because we're going to learn what happened when they didn't quite keep their security as tight as it should have been.
But what exactly is equifax, besides just holding that report?
Well, as I said Equifax is one of the three major credit reporting agencies in the United States, alongside Experian and TransUnion. The company plays a crucial role in the American financial system, providing a range of credit-related services that impact consumers, businesses, and the economy as a whole. Any impact to a company like this is guaranteed to have ripples out to hundreds of thousands of people.
Its importance stems from its role in collecting and managing vast amounts of consumer credit information, which lenders and other institutions use to make informed decisions about extending credit and managing risk.
At its core, Equifax is primarily a repository of credit information. It compiles and maintains detailed credit reports on individual consumers, documenting their borrowing and payment histories. Equifax gathers this data from various sources, such as banks, credit card companies, auto lenders, and other financial institutions, as well as public records like bankruptcies and tax liens. The information collected includes details about credit card accounts, loans, mortgages, payment history, credit limits, outstanding balances, and any negative credit events. It also includes personal information like names, addresses, and Social Security numbers to ensure accurate identification.
Latch on to that last line real quick because that's your impact right there. If Equifax is breached, and your information is stolen they have almost everything they need to know about you to start doing things like applying for credit cards, taking out loans, and more.
I know I'm talking bad about the impact but that's not to say they're not important because credit reports generated by Equifax serve several critical functions:
Credit Evaluation: Lenders, from major banks to local credit unions, rely on Equifax's credit reports to assess an applicant's creditworthiness. The information helps them determine whether to approve or deny a loan application and, if approved, what terms to offer, including interest rates.
Risk Management: Financial institutions use Equifax's data to evaluate the potential risk associated with lending to a particular individual. This data-driven decision-making helps mitigate the chances of bad loans, which could have adverse effects on their financial stability.
Consumer Access: Consumers have the right to access their own credit reports, allowing them to monitor their financial standing, dispute inaccuracies, and take steps to improve their credit scores. This access is essential for individuals seeking to secure credit, housing, and even employment.
Fraud Prevention: Equifax helps identify identity theft and credit fraud by monitoring for unusual or suspicious activity on a person's credit report. If someone tries to open credit in your name without your knowledge, Equifax's data can be used to detect and address this.
Business Decisions: Companies beyond just financial institutions use Equifax's services for various purposes, such as screening potential tenants, assessing business creditworthiness, and making informed decisions regarding partnerships and contracts.
Equifax's importance in the financial system and broader economy is undeniable. The accuracy, timeliness, and completeness of its credit reports directly influence the availability and affordability of credit for consumers. A positive credit history can lead to lower interest rates, increased access to loans, and better terms on credit cards. On the flip side, a negative credit history can limit financial opportunities and result in higher costs for borrowing.
However, Equifax's significance also highlights the correct concern that comes with it related to data privacy and security. Given the sensitive nature of the information it holds, Equifax and similar agencies have a responsibility to the citizens of this country to maintain stringent security measures to protect against data breaches and unauthorized access. Unfortunately, we're about to find out that the responsibility was not necessarily a mutually understood agreement.
Now I said we're starting in March, but that's not when the hack that happened occurred, that won't be for another few months. But, one of the big dominos that made it possible was about to fall and set things in motion that would bring us there. So before we move on to the start of the hack, I want to talk about Apache.
I'm not talking about a Native American tribe, or a helicopter, I'm talking about a widely utilized piece of software that is the backbone of many websites. At its core, Apache refers to the Apache HTTP Server, often just shortened. It's not something you directly interact with like an app on your smartphone; instead, it's the invisible powerhouse that makes websites and online services accessible to you, acting as a middleman between your web browser and the websites you visit.
Think of Apache as a web host for websites. When you type a URL into your browser, Apache is often the software that listens to that request and serves you the webpage.
I want you to think about Apache like a pizza shop. You're at home, and you decide that you want to place the order. In this little analogy the pizza is a website. Now, the first thing you do as someone that's hungry is call them up and place the order, you request it. Well, with a website we'll say that instead of dialing a phone number we're using a URL and instead of a pizza description you're giving a request for the website. This is what's called an HTTP Request, and inside of it contains all the information that's required to make sure you get the best experience out of a website. You can think of those as the toppings on your pizza.
So that HTTP Request is gonna contain information like the kind of device you're accessing from and the browser. That's going to let it optimize appropriately, maybe determine whether or not a mobile site is needed or a regular one. It'll contain what kind of connection you want, and if you're sending any data or if you are just requesting it.
That all adds up to the pizza place being able to get you the right order, at the right time, with the right toppings and it results in the right website being fed with the right look and feel.
There's a lot more to it but that's about as barebones as I can make it. As of this year, about 1/3 of the population of websites have Apache as a backbone. Sites like Adobe, spotify, ebay, and yes…. even parts of Equifax.
That's all to say that when a security issue is presented in apache, you act quick because not only can it impact your services big time, it's usually on the front end of the internet….directly exposed to any would be hacker.
So when on March 17th, 2017 a Security Bulletin rated Critical came out from apache, many companies jumped on testing and deployment. According to the bulletin itself Apache said that It is possible to perform a remote code execution attack with a malicious Content-Type value. If the Content-Type value isn't valid an exception is thrown which is then used to display an error message to a user. This vulnerability reared itself as a part of the Apache Struts foundation piece of the software and now it's hard not to associate Struts with this vulnerability that would define it for years to come.
So let's talk about what that means. First off, remote code execution, that's just saying that I can serve you something that makes your server perform an action it wasn't intended to. In this case, it was found that the "Content-Type" piece of that HTTP Request we were discussing earlier was the point of entry.
The hack would work like this. When Apache is fed a content type that's defined as multipart/form-data, you can use the language that's structured in to add a bit of your own code. That's all sent through the vulnerable parser and when it gets to your code an exception is triggered. That means that everything there is passed along into an error message with the payload you sent, and when function is evaluated your code could potentially run.
Let's take it back to the pizza shop though and break it down a bit more simply, because I expect that might not have been the most straigtforward explanation. If I'm ordering a pizza I almost always would call up and ask for a large pizza with mushrooms, peppers, and onions. In that order it's like the language that's fed into the content type.
If the pizza place was vulnerable in the same way Apache was, then I could call up and say I want a large pizza with mushrooms, peppers, open the cash register and take out 200 dollars and bring it to me, and onions. Then when the pizza got through the order and went to make it, he'd get confused, look at my instructions, and get me 200 dollars and bring it to me.
Think about all the things a hacker could do here, and don't worry…if you can't they sure did because within one day there was proof of concept and exploitation code out in the world for anyone to use. And I mean anyone, there's a tool called Metasploit out there, it's a repository of enumeration and exploitation tools. A lot of people like to joke that it's the backbone of many a script kiddie, but that shouldn't take away from how insanley powerful it can be. The tool is built into many hacking distros and toolkits and the ease of accessiblity to the struts exploit code meant that companies needed to be quick on their feet to patch because time to exploitation was no longer being written in days and weeks, it was down to hours and minutes before vulnerable servers might be exploited.
If this is left as is, then it's essentially an open invitation for someone to come in and set up a tunnel straight into your server that the website is hosted on. And because it's on the internet and this request is fairly basic, it wouldn't be hard to automate searching for vulnerable servers.
Speaking of vulnerable servers…..let's go back to Equifax now. Because Equifax had one vulnerable server that was found quickly and I expect, would end up getting a lot more traction as a result of this.
The website that we're going to talk about was Equifax’s online dispute portal. That site is a web-based application that allows an individual to upload documents to research and dispute an inaccuracy in their Equifax credit report. So say that something popped up on my credit report that said "New account opened" and it's a credit card but I didn't register it, I might go to this portal to say "Hey, that wasn't me. This isn't a card in my name or that belongs to me, please remove it". Or maybe something went to collections and it's still on the credit report but there was an agreement with the collection agency to remove it once it was paid. This is the portal you'd go to upload documents supporting that and get it removed.
Needless to say, it was pretty important, and in this case pretty vulnerable to that Struts vulnerability.
Well, here's where things start to get a bit interesting because the later on, Equifax would bring in the company Mandiant, now owned by google, to assist with incident response, forensics, remediation, and major efforts regarding this case. Mandiant determined that the first successful exploitation of the struts vulnerability against equifax occurred on March 10th, less than 2 days after it was disclosed and made available on MetaSploit.
But that's not the hack that we're concerned about here. If it was, it would almost be understandable what happened because a 24 hour patching turn around can be tough. Experts believe that this was either an automated scanning tool, or some inexperienced hackers that might not even have realized what they had found. Like I said, when something is straight up exposed to the internet like this, there's likely to be scanners looking for this vuln to exploit all the time.
No, March 10th is not our date. We're going to move to May, more specifically, we're going to May 13th. This is when the next few dominoes on the line of poor practices started to rear themselves. Because just getting into a web portal doesn't inherently mean you've got keys to the castle here. And it still doesn't mean that you have time to react. The hackers here had a couple options. First they could smash and grab and be loud. If they wanted to, they could light up the network, probing whatever they could and trying to get anything they could out before vulnerabilities were patched and they were eradicated.
The other option, and the one that was taken here, was that they could take their time and learn to use what's on the network. In this case, the overall timing of the breach lasted from May through July of 2017.
Over this period the hackers would find two major security no-no's. The first was that there wasn't much network segmentation. Network segmentation in this case means that you'd keep servers that handle sensitive data in a part of a network that might not be able to be accessed by servers handling standard user data or non-essential tasks. It's like having no interior walls at all in your house, even in the bathroom. Traffic could move around without check in some cases and it meant that when a server was popped and owned by the attackers they would have that much more capability for persistence.
The other thing that was noted as being found on the network? Clear text password credentials being stored on systems. This means that somewhere in that slew of systems there were text files that you could get into without a password, or maybe internal wiki's, that had passwords that were entirely valid.
So let's tally it up a bit and look at the failures here.
From March 9th to May 13th no patch had been applied. This was critical, and we'll get around to what happened here but that was a major failure, the lack of patching follow through and control. Now the earliest reaction from this was the correct one on Equifaxes part. On March 9th administrators were told to apply the patch on affected systems. That phrase there, affected systems is the critical word I'd imagine may have contributed to part of this blunder.
According to statements and articles, the employee who should have done so, didn't because the vulenrability scans that were supposed to identify unpatched systems didn't detect this iteration. They would run scans but they didn't detect anything. This could have happened if segments of the network were missing from scans, if scans needed credentials but didn't get them, or even if they ran the scan before the signature for detection was released.
That's just speculation on my part, it's not super clear what was happening on their team beyond the fact that Equifax didn't detect the problem and didn't patch it. On top of that, Mandiant, in a separate incident, had already warned Equifax about unpatched systems being a major problem in their environment.
Then we have a lack of network segmentation, no security around the rooms of the house, so to speak.
After that we had plain text and easily accesible passwords. Sure, let's give hackers keys to valid accounts. If they get cutoff from their exploit access now they probably have valid access to replace it.
And then there's one last thing. You see, this data is so sensitive that it needs to be encrypted in traffic. You don't want anyone to be able to sit on the network and just listen and capture secrets. Well, Equifax used a tool that would allow for traffic to be encrypted in transit, decrypted, inspected, and monitored for suspicious activity, and re-encrypted. Well, one of the components that makes up that kind of infrastructure needed to be replaced and renewed with a new certificate to validate it annually. Turns out equifax never really did that. In fact for this specific tool they wouldn't until nearly 2 years later. But if that had been working, then encrypted traffic would have been inspected and may have caught the exfiltration of all the data taken from the many databases that were popped by these hackers.
All in all 51 databases were compromised in this hack, leading to the exposure of Social Security numbers, names, addresses, and more. In the breach, the hackers managed to get the information of around 143 million people, more than 40% of the population of the united states. Imagine waking up one day and just all of a sudden being told all the information you need that could help you make a financial decision had been stolen. And not only that but odds are many of your friends and family are in the same boat.
And equifax? They didn't know they were being hacked until July 29th….over 2 months after this instance of exploitation of struts. 2 Months of continuous failure of security tools and practices.
There's a concept in security we talk about a lot, it's called defense in depth. The basic premise is that you don't rely on one piece of security to get you through things. You layer controls, and in thoughtful layering of security measures even if one is breached there is usually another somewhere to pick up the pace or identify issues.
I've also heard some people call it the swiss cheese method. If you think about security as a piece of swiss cheese, there's hole in it that someone can look through right? Well, toss another security tool in there, another piece of cheese. There might still be an available peeping hole but because each slice of cheese is different you also might have covered up a good chunk of it. Keep adding slices of cheese and that's defense in depth.
I think in this case equifax might have just been lactose intolerant I guess, because the swiss cheese method failed spectacularly.
Who did it
You might be wondering now….who? Who hacked equifax? Was it a kid out of Arkansas? Was it North Korea?
Well, as the incident was playing out from the public view several theories emerged regarding the identity of the perpetrators, but one of the most notable theories suggested that the breach was orchestrated by a state-sponsored hacking group. Some experts pointed to China's involvement due to the sophistication of the attack and the potential value of the stolen data for espionage purposes.
Another theory implicated the Russian hacking group known as "APT 29" or "Cozy Bear," which has been associated with various high-profile cyberattacks and has strong links to the Russian government. This theory suggested that the breach was part of a broader campaign to destabilize U.S. institutions and undermine public trust. Cozy Bear's modus operandi aligned with the Equifax breach in terms of scale and sophistication.
Ultimately, cyber researchers basing patterns on previously similar attacks, and the United States would attribute this to the Chinese government.
In an article on CSO Online it's noted why the Chinese government itself might be interested in something like this.
They said that quote "Investigators tie the attack into two other big breaches that similarly didn’t result in a dump of personally identifying data on the dark web: the 2015 hack of the U.S. Office of Personnel Management, and the 2018 hack of Marriott’s Starwood hotel brands. All are assumed to be part of an operation to build a huge “data lake” on millions of Americans, with the intention of using big data techniques to learn about U.S. government officials and intelligence operatives. In particular, evidence of American officials or spies who are in financial trouble could help Chinese intelligence identify potential targets of bribery or blackmail attempts."
And back in February 2020. The United States Department of Justice did something that was kind of unusual; they decided to formally charge four individuals who were part of the Chinese military. This move in itself was seen as largely symbolic. It wasn't like China was going to extradite them out to the US for trial, after all these were foreign intelligence officers. I think this was largely to set a precedent that a new level of scruting was being paid from the US Government as a part of the response.
And speaking of response, let's talk about that, both from the side of Equifax and the US Government.
Let's start with Equifax. Because you'd think that after the scrutiny of such a major security blunder, they'd handle everything by the book and cleanly. Well, that wasn't really the case it seemed. They wouldn't announce the breach until September 7th. About a month and a half after they learned of the attack and several months after the initial breach. The first thing they did was establish equifaxsecurity2017.com , a site for people to go and learn about what happened. It contained announcements regarding the issue, frequently asked questions, and operated as a general information hub.
Here's a segment of the first announcement they put out on September 7th of 2017. Almost four months later.
The information accessed primarily includes names, Social Security numbers, birth dates, addresses and, in some instances, driver’s license numbers. In addition, credit card numbers for approximately 209,000 U.S. consumers, and certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers, were accessed. As part of its investigation of this application vulnerability, Equifax also identified unauthorized access to limited personal information for certain UK and Canadian residents. Equifax will work with UK and Canadian regulators to determine appropriate next steps. The company has found no evidence that personal information of consumers in any other country has been impacted.
Equifax discovered the unauthorized access on July 29 of this year and acted immediately to stop the intrusion. The company promptly engaged a leading, independent cybersecurity firm that has been conducting a comprehensive forensic review to determine the scope of the intrusion, including the specific data impacted. Equifax also reported the criminal access to law enforcement and continues to work with authorities. While the company’s investigation is substantially complete, it remains ongoing and is expected to be completed in the coming weeks.
“This is clearly a disappointing event for our company, and one that strikes at the heart of who we are and what we do. I apologize to consumers and our business customers for the concern and frustration this causes,” said Chairman and Chief Executive Officer, Richard F. Smith. “We pride ourselves on being a leader in managing and protecting data, and we are conducting a thorough review of our overall security operations. We also are focused on consumer protection and have developed a comprehensive portfolio of services to support all U.S. consumers, regardless of whether they were impacted by this incident.”
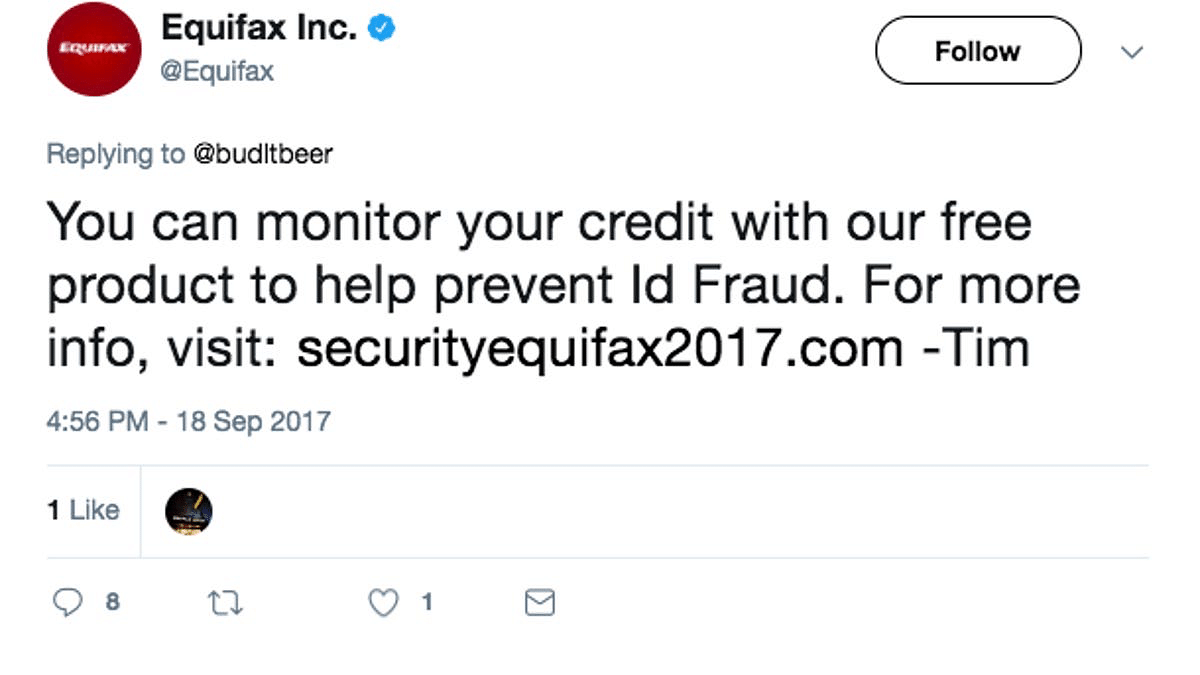
So we're getting fairly standard corporation speak, but it does strike me as odd that they almost try to downplay the impact while then going on to say how insanely massive this breach is. There would continue to be some interesting blunders coming up too. Because after that domain was registered, they didn't really bother registering similar domain names. So they made equifaxsecurity2017 but didn't think about maybe also getting securityequifax2017. This might not have come to your immediate thoughts but as a security practioner this kind of domain look-a-like hijacking is super common. Well Nick Sweeting, a software engineer, decided to buy the domain and make a look a like page. Lucky for everyone it was largely the same and not malicious. Some of the only differences were the inclusion of lines like ""Why did Equifax use a domain that's so easily impersonated by phishing sites?"
Sweeting would receive over 100k hits on this website, and it would go so far as to be tweeted out as a place to monitor your status….BY THE OFFICIAL @EQUIFAX ACCOUNT.
That's right, the official Equifax twitter would post multiple tweets directing users to this site that wasn't there. So imagine the number of actual phishing campaigns that would start to pop up with sites using the same tactics. I've got a picture of one of the tweets up on the website in the transcript of the episdoe at whattheshellpod.com , so go take a look. I'l also be posting it onto the shows instagram if you want to see. That's @Shell_pod
There was one other piece of cake that was found on the website, it turns out Equifax wanted to try and shake as much legal liability from you as they could because in the terms of use there was this section that read quote:
AGREEMENT TO RESOLVE ALL DISPUTES BY BINDING INDIVIDUAL ARBITRATION. PLEASE READ THIS ENTIRE SECTION CAREFULLY BECAUSE IT AFFECTS YOUR LEGAL RIGHTS BY REQUIRING ARBITRATION OF DISPUTES (EXCEPT AS SET FORTH BELOW) AND A WAIVER OF THE ABILITY TO BRING OR PARTICIPATE IN A CLASS ACTION, CLASS ARBITRATION, OR OTHER REPRESENTATIVE ACTION. ARBITRATION PROVIDES A QUICK AND COST EFFECTIVE MECHANISM FOR RESOLVING DISPUTES, BUT YOU SHOULD BE AWARE THAT IT ALSO LIMITS YOUR RIGHTS TO DISCOVERY AND APPEAL.
So by checking if you're impacted, you can't sue. I guess it's schroedingers class action then. Just sign on and hope you're impacted?
The site also offered a way for you to freeze your credit, get free credit monitoring through them (just for one year though, I mean come on you gotta be reasonable with the company that leaked your identity right?)
And after all was said and done the class action lawsuit was won and equifax had to pay out it's victims. Want to know how much money was given to victims for this? 125 dollars. Your personal information, your identity, was worth less than 150 dollars when all was said and done, plus some short term bandaids.
This was a victory, but also to me seemed like such a slap in the face. The company would continue going on, while citizens would have to live with the possibility that they could wake up one day in ruin.
But let's wrap up with what ended up happening @ Equifax. What did this really cost them?
Well, the C-leadership would end up being almost entirely rolled over. That included one executive that was charged with insider trading after making decisions in perparation for the announcement of the incident. The lawsuit landed them between half and three quarter of a billion dollars in payouts. And lastly they spent a whopping 1.4 bullion dollars on the incident response including new systems, security tools, and employees to cover the access.
So let's call it a cool 2 billion dollars. So there you have it, a 2 billion dollar prices tag for 40% of the countires personal data. An interesting metric to think about.
I think I'm done with the equifax side of things for the episode. I want to get into this weeks end prompt from the community.
The question I've got this week comes from the shows instagram. It comes from user "a_birds_eye_view". They asked "what's really good with this winrar threat?"
So a little background here, I'm assuming this is a question asking what the deal is with the recent news about winrar being hugely exploited. Winrar is a massively popular file archiving tool, if you don't use winrar you probably use 7zip. Basically, if you have a .zip file, this is a tool that can be used to unzip that, or archive a bunch of files into a smaller singular compressed archive. There's a lot more to it than that, but this is the crux of the application.
Well, back in August RARLabs patched a vuln that it turned out had been exploited since at least April. The way the vulnerability works is a little bit complex but I'll do my best to explain it.
The vulnerability to advantage of when winrar would expand certain archives in some situations depending on how the files were structured and combined it with a unique circumstance that would occur in windows when some kinds of files were opened.
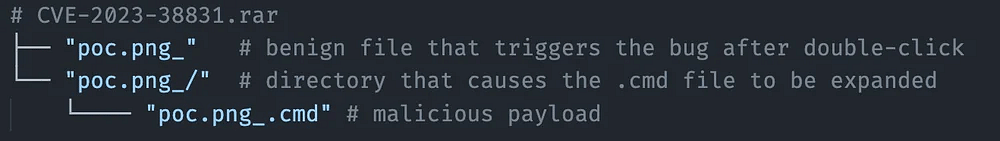
I'm taking this example from the google writeup on how it works. Because I think it's simple and I can include a screenshot from their writeup. The exploit itself relies on spaces in files in the archive.
If you have an archive for example that contains poc.png with a space after png and a directory called poc.png space, then the way winrar handles that is going to be look at both of those, see the directory name matches that selected initial file name and instead extract both the selected file and the files inside a matched directory to a random temporary directory.
Now normally that in and of itself isn't too bad. But in this case, imagine if in that directory there was a subfile with the same name again but a .cmd extension. That's a commandline script and might contain a malicious payload, you know code that would run even if you didn't want it to if you opened it up.
So now when windows is handling this expansion it's supposed to call certain internal functions to support it. I won't get too heavily into it but basically we're tricking windows into looking into the directory, finding and executing the first file with an extension matching any of the hardcoded ones: “.pif, .com, .exe, .bat, .lnk, .cmd”. And then running it. In this case that's the malicious cmd file we've placed.
I've put a screenshot in the transcript as well so you can see.
Now where this all made waves was that this exploit chain has been used for quite a while. One of the major groups using it was Russia. The specific group in their Armed Forces was SANDWORM, a segement of their General Staff. Recently they've successfully used it to launch a phishing campaign impersonating a Ukrainian drone warfare training school. Using a lure themed as an invitation to join the school, the email contained a link to an anonymous file-sharing service which delivered a benign decoy PDF document with a drone operator training curriculum and a malicious ZIP file exploiting the vulnerability. On top of that it's become aware of this vulnerability being used to target critical infrastructure and financial institutions around the world, including the US.
So we've got a lot of active exploitation going on in areas that camn make a large impact. I think that's why it's making the rounds a lot, when you get a vulnerability like this that weeds it's way out of the cyber specific news and into the public limelight, it tends to get prioritized more heavily. That's when you'll have executives occasionally piping in and asking where you stand with it. The big problem is actually similar to struts here. Because proof of concept is relatively easy on this, you'll see a lot of exploitation. That's not to say there aren't going to be a lot of controls available to prevent it from happening or alert on it's occurrence, but as we've seen this episode things can go south. Birds Eye, to sum it up. High value targets + a lot of news + easy exploit = people making a lot of noise about it. Hope this has given a little insight to it.
So that's that for this week. I'm John Kordis and I hope you've got a better idea of what happened with equifax, and learned a bit about how even the largest and most powerful institutions can be woefully unprepared.
If you've taken the time to listen up to here, thank you. If you want to chat about this episode, please join us in the discord. I love engaging with everyone over there and the link is in the description here, on my website, and on my Instagram profile @shell_pod.
I'm happy to be back and I think you will be too because I've got a couple ideas for new kinds of content that will hopefully be something different than what you're used to, and help me try some fun projects. So to sign off, I'll just say thank you. Especially to those of you that are still supporting me on patreon. There were a bunch of you that I think knew I'd be coming back even before I did. So j.s , Stephen, k1lby, Frank, J, Adon, Ben Sweetnam, Ben M, John, Chris Finik, pseudo, rkaFLDvXub, last but never least, I use pot of greed to draw three additional cards from my deck….thank you. If you want to join their ranks, you can find me at patreon.com/whattheshell Let's keep this truck rolling and I'll see you all next episode.