Let's climb olympus, talk money mules, and dive into some malware from the late 00's and early 2010's.
Patreon: https://patreon.com/whattheshell Discord: https://discord.gg/mBPbWcVRYR Twitter: https://twitter.com/shell_pod Instagram: https://www.instagram.com/shell_pod/ Website: https://whattheshellpod.com
Intro
Have you ever felt like someone was watching what you were doing on your computer? It's a little paranoid, I know, but sometimes it just feels like every key I type is being looked at. Hell, I used to wonder sometimes if I should just open up a notepad and type "I know you're watching" and just see what happens. Alright, maybe I was never really that extreme but I think we've all felt that way before. Maybe we saw a popup or something that disappeared quickly, maybe something just doesn't feel right about your machine today. Most of the time, it's nothing. But what if it wasn't? What if some mythical group actually was sitting on top of your machine. At the peak of what could be called a Mt. Olympus of personal data. What could they do?
Well, in the early 2010s, this wasn't just some Myth. I'm John Kordis and today I'm taking you on a hike up Mt. Olympus itself and we're going to talk about a malware that was considered one of the biggest issues we'd seen up to that point. We're going to have some words about Zeus.
Joan and Dartmouth MA
Let's start with a little story I found curtousey of a news report on the situation. We're going to start our journey in 2010, in a town in southern Massachusetts called Dartmouth. Dartmouth is a smaller town, and home of one of the states universities. It's a nice place and full of decent people. One of those people is a woman named Joan Halwood, who worked for towns fire department. She wasn't a full time employee, just worked from home part time doing payroll and expense balancing.
Honestly, the first surprising thing to me about this whole story was the fact that she was working from home in 2010. But, that aside Joan was good at what she did. Until one morning she signed on and noticed that her home computer that she was working on was, in her words, acting up. She had been experiencing latency issues, slow connections, and it had even crashed a few times. When she realized she wasn't going to be able to get to the point where she could log in to the fire departments account on the bank website, she just decided to go straight to the source and call them.
In her initial discussions with the bank, they were only able to indicate to her that there didn't seem to be anything wrong with her account, as they had sent he wire transfers she'd recently made. The only problem? She didn't make any wire transfers. By the time she actually could log in, she was able to identify that six transactions total had taken a toll of about 400k dollars out of the account, putting it almost down to no money left. For reference, according to her that was about half of the annual budget for the fire department.
And it this point she still didn't know what happened, who did it, or why. I can't imagine how that must have felt for her. I think I'd have had a panic attack in that situation. But as it turned out, she wasn't alone in this situation.
Across the world, other institutions were being hit by the same problem and this wasn't the first nor would it be the last. In fact, by this point it had been estimated that over 3.6 million machines in the United States had been infected with whatever was ruining Joan's day.
Some of the other places that had been hit? Well there wasn't much of a rhyme or reason to who was targeted. Individual people were hit, a bakery in Chicago, a catholic diocese in Demoine Iowa lost 700k dollars, and a contractor for the Michigan Defense Agency lost 5.2 MILLION dollars. All in all by this point it was estimated that around 70 million dollars had been stolen by the malicious actors in this case, and according to FBI Executive Assistant Director Sean Henry, it was all by the same group. So that leaves is with a few questions now. What did this? How does it work? and Who did this?
What Is Zeus?
Let's start with the 'What' of it all. This is where we get to the namesake of the episode because the malware that did this was called the Zeus malware. Zeus pulled just about every trick you can imagine to get the information it needed it to operate. The primary goal of the malware itself was to steal banking information. But before I tell you how it did that, I want to lay one thing out for you in terms of what the security landscape looked like.
Think about your browser. Think about Chrome or Firefox, or if you're a sociopath Edge. You know how when you visit a website you often see the little lock next to the address? That's to indicate it's using a secure connection, called HTTPS. That's Hyper Text Transport Protocol Secure. When you're using this, traffic is encrypted and harder to read, and it is the standard for internet browsing. That wasn't always the case. In the past, sites may have been using unencrypted connections which were much more prone to being snooped. That's not to say that was a primary vector here but I just want to let you know what the landscape looked like. Because this malware had been active for several years by the time 2010 came around. And in May of 2010, that was when google said "Hey start using HTTPS, it's safer and we'll be deprioritizing standard http sites". So we weren't nearly as protected as we were now. It's like right now we've got a barbed wire fence and back then we had wooden farm fences that were only good for keeping the cattle in. Not really a whole lot if you've got a creative threat.
Okay so you're probably at home thinking "Cool story John, but what did Zeus actually do". And we'll get to that but first let's talk about how it got on your machine and how it stayed there.
What I'm about to say shouldn't really surprise anyone but Zeus was delivered by three primary attack vectors. The first, was phishing. You know someone trying to make you click a link that's meant to look like something you actually should be viewing, and the thing your company sends a simulation out a couple times a year to make sure you're actually paying attention to your inbox. The second is just straight spam. That could be spam emails offering explicit goods or even an a spam ad that might launch a popup for you to click. The last primary vector is something that I don't think we've really covered on the show before and that's called a drive-by download.
That's to say it's a download that you didn't intend on happening or maybe didn't even know it happened. It could be something that was launched in the background, included in something else you might have downloaded, or maybe even installed with software you were putting on your machine. Have you ever installed something that would basically advertise several other programs as a part of it's install process? Well, it's possible that this malware might have been one of the things that was trying to sneak it's way in while you were clicking 'next' over and over just trying to get through your install.
So, now at this point you've gone ahead and fallen for the spam, clicked on the enticing email, or downloaded Zeus to your machine. What's it going to do next?
Well, the original variant of zeus was very good at hiding itself. In these early iterations you'd be able to find activity of zeus if you knew what to look for. Essentially, depending on how much admin access the user that was infected had, would determine where loot was hidden. If you were a full admin you could find directories created in the system32 folder of your machine. The system32 folder contains core components to your windows operating system and an average user would almost certainly not be able to identify something malicious just by looking at the contents of the folder. Also, on a side note, never trust anyone that tells you the fix to your problem is to delete system32.
The malware itself at that point was located in the sdra63.exe, and it's lute was kept in a folder called lowsec. If you weren't admin, those details wouldn't change, except in that they would be located in the app data directory which is usually a hidden directory on your machine, accessible but not inherently visible.
Depending on those same capabilities, Zeus would then make some key internal changes to the registry if it could. The target here was to make sure that it started up with administrative privileges, effectively giving it read/write access wherever it wanted and free reign over your machine.
So now the pirates have arrived, they've dug the hole where they're going to bury the treasure, but where's the chest? What's in it? Let's talk about how it stole your data because what it did was incredibly sneaky. While some of the targets of zeus were random in who they were, once it was on your machine it's goal was relatively singular. It looked for financial data specifically. It was looking for targets on your machine that could provide instant value.
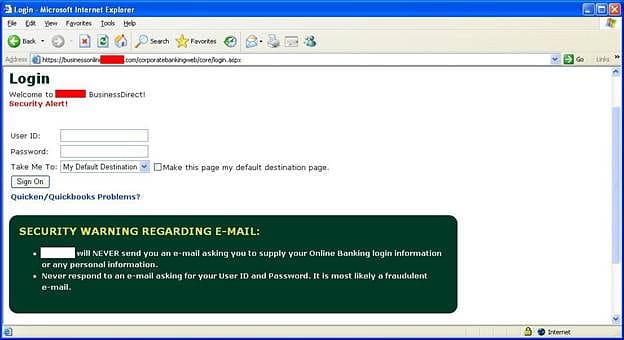
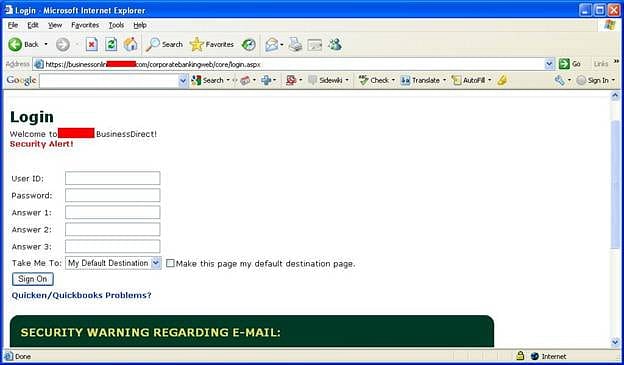
When it was on your machine it had a few key capabilities. Those capabilities included it's starting process which would steal credential information from you machines by taking it from your web browser or the internal protected storage that was housed in windows. From then on out it could wait until it detected that you were going to a financial site to try and work it's magic. If it detected you were going to the bank site, it might launch one or all of these capabilities. First it could engage a keylogger, making note of everything you typed which might inherently include your email or username and password. It could take a screenshot whenever it liked of the page you were on. And one of the crazier things it could do? It could alter the page you were viewing slightly. So for example, if you were presented with a login for a username and password. What Zeus might present you is a new page asking you to confirm your password and answer the security questions. I've got an example on my website of what it might look like. You can find it in the episode transcript at whattheshellpod.com. But I mean, I don't think many people would think that extra layer of verification was super abnormal. But with it, they've got all the details they need to steal your bank account.
The page looks exactly the same, even going to far as to include a warning about potential fraud and how the bank will never email you directly asking for the above information.
Now one thing that was interesting to me was how Zeus had such trouble being tracked down. After all antivirus wasn't new at that point. Well, Zeus had this frankly cool ability to re-encrypt itself each time it infected someone. You might think that's not a lot but what that means is each time it re-encrypts or reinfects, it technically is slightly different. Different to the point where it evades detection in a lot of cases. It would be like saying I'm the program and the police are the antivirus right? My clothing is the encryption in this little metaphor. They've got my last known attire, but every time I leave a building I change my clothes. They know enough about me to recognize where I am after I've been there, but not enough to identify me before I rob the place because I keep changing my outer appearance. That's what the encryption is doing here. Making it harder for antivirus to outright identify and act on it before anything happens.
So Zeus is on your machine, it's gathering this data and storing and then it'll stealthily send that information up to a command and control server. That's a server somewhere that the attacker can log into to run commands on infected machines.
And if you're brain is starting to tingle a little bit there, like maybe there's something you can do with that little capability, you're right. There is. Because not only was zeus. Because the original person that coded it was really interested in making a profit out of this, it was also able to be used a botnet, and rented out to whatever person or group wanted to use the machines in an attack. So remember again, as of the start of this episode in 2010, that's over three and a half million machines infected into the botnet.
But that does pose a point there. I said whoever coded it wanted to make a profit, but who was it? Well this operation that was making headlines was spearheaded by a group
Who made it?
Well toward the end of 2010, the FBI started to really go full force against whoever was running this whole thing. That's when they announced that they had dropped a number of arrests in the ring that was responsible here. The group, was mainly international with much of the crew operating out of the Eastern Europe. The FBI archive said that quote
With our law enforcement partners in the United States, the United Kingdom, Ukraine, and the Netherlands, we[The FBI] announced the execution of numerous arrests and search warrants in multiple countries in one of the largest cyber criminal cases we have ever investigated.
“This was a major theft ring,” said Gordon Snow, assistant director of the FBI’s Cyber Division. “Global criminal activity on this scale is a threat to our financial infrastructure, and it can only be effectively countered through the kind of international cooperation we have seen in this case.”
I've got the wanted photo of the group on my website as well in the transcript, but they made major arrests and found that while they managed to get away with around 70 million like we discussed earlier, the attempted amount…included the dollars that might not have been withdrawn yet, or were held up thanks to bank protections, totaled to almost a quarter of a billion US Dollars. There's 20 people on this wanted poster, so if each of them got an even split? It's a little over 10 million a piece. They could have had enough to live happily without a care if they really wanted to. All in all though, not including the mastermind 20 there The FBI detained over a hundred people, who were charged with conspiracy to perform bank fraud and cash laundering, 90 of them in the USA and the rest in Europe. This split is beccause of something we'll talk about in a bit, the people who were money mules.
But one person isn't identified yet. The creator. According to cynet and other sources this man was named Hamza Bendelladj, an Algerian citizens who had aliases of "The Smiling Hacker" and "BX1". It would take several years, with him being involved in the top 10 most wanted hackers by both the FBI and their sister across the pond, Interpol, before he would end up in the United States, where a US Court would sentence him to 15 years in prison, with 3 more years of probation. He was extradited in 2013, charged in 2015, so at this point he's barely over halfway through at best.
What's particularly interesting is that in 2010, several years before this, he took to the internet to say that he was "retiring". He sold the source code of Zeus to one of the competing malware groups, the creator of the SpyEye trojan.
It really was about the money I guess. I wonder if under the table pension he'd get from the sale of Zeus was worth it?
It wasn't just the FBI that helped either. There was a kind of citizen brigade that came in with the assist here. The primary civilian leading this charge was a member of the University of Alabama staff named Gary Warner. Gary, with the help of a kind of vigilante monitoring group that affiliated itself with the FBI called Infragard, were able to find some commonalities and information that led to the major developments which tied this to hackers in Ukraine.
Not only that though, he and the team found out the secret sauce of how they got the money out. Because even then, if you just transferred it to your own account there's two problems. First the bank knows where the money is. Second they know who you are and can just shut the account down.
This was a game of trickery and timing. This group knew that they had to get the money out quick and clean. So how did they do it? Well what they would do is use some of the accounts they'd compromised as transfer accounts. So the process might go something like.
Let's say I'm the head of the hacker group here monitoring an operation. In this operations we've compromised 2 accounts; one for Shell Pod Inc and one for Nate Shelly. If I transfer both accounts funds to me, then I've got the problem of people knowing who I am. So instead I'll wait. And while I wait, I'll hire someone in the US to go withdraw money from one of the accounts. The added benefit is that local transactions like this are much less likely to be flagged by the banks either. Once the cash was withdrawn they just need to send the money back to me using something like Western Union. You know what, I'll even give them a 10% commission. So now I can transfer both, quickly have the person stateside withdraw it, then send it to a fake Western Union I've got to avoid suspicion.
Who might do that though? Well, unfortunately gullible people and down on their luck individuals. If you remember ever getting spam for working form home and making 3,000 a week doing it that seemed to good to be true, this could have been one of the things you were doing. That was again, back in the late 2000s and early 2010s when Work from home was less of a common place thing so this would have been appealing.
What Gary also found was that this kind of scam was just the first in an even bigger line of fraud. The team eventually would upgrade their process and instead of hiring Americans to be the mules, they would supply Eastern European students with fake identities and passports. The goal for these students? They'd go to the US, open a real bank account with the fake identification, then wait for it to fill, withdraw, take your commission, send it over, and repeat. The added benefit here was that these were real accounts the attackers controlled, and didn't need to worry about information changing on them. The students would land a pretty penny out of this and while some weren't made aware right away they had to suspect something when up to 250k at a time was transferred.
That's up to a 25000 dollar payout!
They found the cash mules partly by taking the bank information they could get and Gary said to his students 'find these suspected mules' as a class project. From there it turns into a game that we're pretty wildly familiar with, OSINT. The students were able to track down a lot of these suspected mules just through social media!
One of them, well I've got her picture on my site in the transcript but you can see her actively flaunting the cash withdrawl. She's got a hand of fanned out 100 dollar bills. I do wonder if this is her cut or the full transfer but either way it seems like she had some idea of what was happening here….

Once this information all caught on, that would lead to the point where the arrests were made in 2010, and the 90 or so stateside individuals that were helping with the operation were arrested.
That's not really the end of it all though, but it is where I'm drawing the line on this episode. You see something else happened besides the arrests that some of you might be curious about and that's the sale of the zeus malware. With zeus being sold, doesn't that mean that it could still be out there? And boy howdy are you right. There are hundred of thousands of variants of Zeus out there now. It started spreading like wildfire, even going so far as to make descendants of the Zeus malware that are as notorious, if not moreso, than it's originator. Malware like Zbot and GameoverZeus spawned from this. And I am eventually going to get into a part 2 of this where we talk about the generational differences and nuances of the variants, but I wanted to make sure you all knew that this story still isn't over. It's just constantly evolving. So for this week, that's it, I'm John Kordis and thanks for listening to me explain What the Shell happened with the mythically insane Zeus malware.
If you want to hang out you can join me and some of our fans in my shows discord, the link to that and my socials are in the description of the episode and lastly there is something else that I wanted to talk to everyone about. You may have noticed that "Hey there's no ads in this show, that's pretty neat." That doesn't mean the show doesn't cost money to make, so to help offset the cost I launched a patreon, and it's as simple as going to patreon.com/whattheshell. There's a couple different plans including varying levels of bonuses; want to just support the show, want some discord flair in the server, hell maybe you even want to commission a mini episode? It's all there. But I'll let you decide if it's worth it.
Lastly, speaking of signing up, here's a thanks to all the existing patrons for helping me keep the show running. So thank you and I apologize on the pronounciation here:
Benjamin Sweetnam
Jon
Kristian Odegaard
pferd
Chris Finik
Ben Marcaurelle
pseudo
Tyus Ashworth
rkaFLDvXub, which I swear is how it's typed out.
and, last but not leat the user that's continuing to test out the limit of characters in his username "I use pot of greed to draw three additional cards from my deck" Thank you for supporting the show, it truly means the world to me. I'll see you all in a bit for another episode of What the Shell?