Let's shine a light on what the dark web is, and what's going on down there.
Patreon: https://patreon.com/whattheshell Discord: https://discord.gg/mBPbWcVRYR Twitter: https://twitter.com/shell_pod Instagram: https://www.instagram.com/shell_pod/ Website: https://whattheshellpod.com
Darknet Diaries "Welcome to Video": https://darknetdiaries.com/episode/131/
- Intro
I want to lay out a situation that I'm sure most of us have experienced before. You're at home, taking a break from work and watching a movie or a tv show. The scene appears and the hacker character is trying to find someone online only for them to have been "hiding in the dark web". Or maybe they're talking about the bad guy they need to hunt down that's selling weapons on the dark net. Have you ever stopped for a second and asked yourself "okay but like, what is the dark web?". For most people, I think they think it's just this big scary impenetrable place that only the most elite hackers can get into. Well it's not some unknown and mystical area that you need to pass a test to get into and It's not just some Deus ex Hack-ina that script writers can use to hide their bad guys.
My name is John Kordis, and today I want to guide you down below the surface of your normal internet browsing habits. We're going to dive down deep into the waters of the web and we're going to come prepared so that I can shine a bit of a light on What the Shell is in the shadows of the dark net.
INTRO
- What is the Dark Web
Okay, given that the news often times will exaggerate the dark web and movies just often times are making up their own rules as they see fit, I thought that it would be important to start the episode with a little bit of a breakdown as to what it is. Let's start by talking about the internet as you , the audience, likely know it.
We're going to break this down into three key components. The surface web, the deep web, and the dark web. Now I know we're talking about webs here but I'd like for you to think of the internet in this case an ocean. That's the metaphor we're going with so grab a kayak because we're going in.
The area of the internet that a lot of people use every day is often referred to as the surface web. This area of the web doesn't really require any special credentials or privileges to access. You can think of it as the surface of the water. This part of the internet is the part that gets indexed and archived by search engines like google and Bing. You ever wonder how they get their search results? Well all these different search platforms have bots just combing the internet logging and adding everything they see to their list. They'll get everything that they can that doesn't need any kind of credentials to get into, report back and that's where they all end up.
For our little metaphor you can think of them as a cartographer with a real good pair of binoculars. Constantly searching the surface of the water and mapping it out for anyone to use. Like I said, any site that doesn't require authentication is under this umbrella. So you'd consider YouTube, free news sites, reddit, and sites like that all parts of the surface web. But what if we wanted to go a little deeper? Well, if you wanted to put on your swim gear and go snorkeling, you'd land in the next level down; the deep web. The deep web is what's beyond any kind of authentication. You might not have thought so given the ominous tone of the term deep web, and the fact that it's often used kind of interchangeably by the public with "dark web" but we all use the deep web quite a bit. This part of the internet is the part just below the surface, that search engines can't index as a part of their operations. It's what's beyond the login portals and in the privileged access of those areas.
Here you'll find many things that you use daily like private social media, email clients, bank and health records, and anything that falls under the pay-for-service model. A good example of this might be a news website. The front end is facing the surface web, and that's accessible but some of it might fall into the deep web as that's where they'll put their paywalled articles. The deep web is the majority of interaction on the internet these days I'd wager, as most things we do while logged into our own accounts aren't indexed by google. It's how private chat areas exist like discord. You won't find the What the Shell or School of Movies discord messages indexed on google, you've got to log in and join the room.
So now, with that in mind, we've covered what most people in their day to day lives use. That leaves just one area left. The depths below where you'd be able to swim, where light can't even make it through the water. This is the dark net. The dark net is, in and of itself a subset of the deep web. That's to say that it's under the banner of things that are not indexed by search sites. But there's more to it than that. Not only is it not indexed, meaning that you can't access it without knowing exactly where you're going, access to the dark net is encrypted and you'll need to use special tools to access the sites. This means that not only is it hard to find the sites, but when you do end up visiting them, your privacy is much more protected than it would be. We'll get into that now because the next questions I can practically hear you asking is "John, how do you access it?"
- How do you access it
Well, if you think about the concept of an encrypted unindexed network, you might realize that theoretically that could be more than one thing. Like there's not a monopoly on making a "Dark Net". There is however, a behemoth. The biggest name in the dark net that is thrown our there is usually TOR. That's T. O. R, The Onion Router. You may have heard of the term TOR before and this what we're referring to.
It works like this, using an entry point such as the TOR browser itself, you can get access to the dark web. The traffic that's passed through here maintains its privacy and security by bouncing itself through what are called "volunteer nodes" . Then, after the traffic hits the exit node, it will access the site you're looking for. It's really just passing your traffic around to the point where it becomes insanely difficult to trace it back to the originating source.
And you might think, what kind of nefarious group would think up such a convoluted idea. Who would do such a thing and just release it onto the world?
Would you be shocked if I told you it started with the US Government? More specifically, the US Naval research lab? Back in the 1990s one particular group of individuals notices that a there was a distinct lack of security on the internet and it would soon, if it hadn't already, be a tool for surveillance and tracking. Michael Reed, Paul Syverson, and David Goldschlag all wanted to work to make internet connections that wouldn't reveal who was talking to whom. With this concept in mind, they thought up the idea of onion routing. If you route through multiple servers and encrypt it on each stop of the way each pass through adds another layer of security. And as with almost all metaphors involving layers, they made it about onions.
It wouldn't really come to fruition until the early 2000s when after Nick Mathewson joined in, the first iteration publicly deployed. At it's start, it had just about a dozen volunteer nodes for passing traffic. Today, that number is in the thousands.
And volunteer is a theme here too. Because TOR isn't some shady group, you can take a look at their website today and read about all of what I'm telling you. They operate in a similar manner to open source coding. They want true privacy for you, and they let you in on it too. They actually published the code to the project so you could opt in to help.
Let me take a minute to read you their mission statement, it goes quote:
To advance human rights and freedoms by creating and deploying free and open source anonymity and privacy technologies, supporting their unrestricted availability and use, and furthering their scientific and popular understanding.
This hit such a strong note that the Electronic Frontier Foundation would begin helping fund the organization and eventually it would grow into a full fledged non profit called the TOR Project.
Now for a long time there was, again that misconception that you had to be a mastermind to get in. That's because initially it was kind of hard. In the early days you'd need to set up a special proxy tool to make your way in and start browsing but nowadays it's as simple as downloading their own browser. It's built off the back of Firefox, and if you're expecting anything other than an internet browser you'll be let down. I have a screenshot of it on the website in the transcript at whattheshellpod.com, so feel free to take a look if you don't want to google it.
The TOR browser offers you a way to browse the surface web and the dark web all from one place. It comes with it's own manual and you can even get a nice newsletter to keep up to date. It's pretty neat and I can't stress this enough, it's perfectly legal to download this. You won't get in trouble just because you have the browser on your machine. Just don't use the browser to do anything illegal that might trace its way back to you and it's exactly like any other browser except a bit more focused on blocking tracking data.
So speaking of legal and illegal, I think it's time we stop talking about how you get to it and start talking about what exactly there IS on the dark net.
Once you're in on the TOR browser, what now? Well let's talk about some of the perfectly safe and legal places to go.
One of the most common places is called the Hidden Wiki. Yeah the darkweb isn't indexed on google or anything but that's not really stopping users from aggregating their own data as the acquire it and putting it somewhere. Getting to the site is the first little challenge because it's not like you're looking for hiddenwiki.com. The link is a nearly 60 character string of seemingly random numbers and letters .onion.
This site indexed as much as it could for the dark web including social media pages and journalism sites. What I'm about to say might surprise some of you. Did you know that Facebook and the BBC have dark web sites? For Facebook, the reasoning is pretty simple. Maybe you want to try and create your account privately, or and this one is pretty common, maybe you want to use the tool to avoid censorship. There are many countries in the world that impose their own restrictions of content on social media, and by using Facebook on the dark web, you'd get around the firewall that your country has in place.
BBC hits the same point, operating it's own news network on the dark web means that if you know how, you can get their news anywhere in the world without fear of censorship because of government restrictions. This stuff right here, that's the good side of the dark web.
There's other stuff that I'm fairly neutral on like dark web versions of reddit or quoara, and dark web tools for things like filesharing. But there's also the stuff that gives the dark web it's reputation. The illegal side.
And I want to go back to hidden wiki again because, since this is the dark web, and they want to archive what they can, hiddenwiki also has the links to a lot of downright horrendous things on it. I'm telling you, it's probably not worth it to go clicking on anything you don't know there because it just isn't worth the risk of stumbling into something that might leave an impact.
So let's talk about that part for a bit. Let's dive into the part of the dark web that grants it the reputation as the kind of place you might find internet Han Solo. There are parts of the dark web that are invitation only, parts that people don't give out the information to to keep private, parts that publicly boast about what they put up there and parts that exist purely to trade or sell illicit goods. These areas are where the public gets it's idea that the dark web is for a level of person that doesn't care about the law.
To talk about some of the kinds of things that you can by on the dark web I'm going to refer to a privacy affairs annual report that publishes an average price index of things you can by on the dark web. These are all things obtained by threat actors, hackers, or anyone looking to make an anonymous buck.
So if we look at credit cards. For 120 USD I could get credit card details with an account balance of up to 5,000 dollars. 65 dollars gets you the logins for some bank accounts with minimum of 2,000 dollars in the account. 15 dollars for credit card details with the CVV number included. If you wanted a specific country you could pay 30 for Australian cards or 17 for US cards. So know this, it's entirely possible that if you get breached and your information gets sold, your value was placed as low as 17 dollars and as high as 120 dollars. For all the trouble you're doing with? This is the value that your information can effectively be sold for. And this is because usually, this information comes in troves from breaches. So this number, multiplied potentially thousands of times, means a big pay day for someone else.
Maybe you don't want to get involved in credit card data exactly, maybe you just want money to appear. You could potentially pay 50 dollars for someone to transfer money from a stolen paypal or Western Union account.
If you wanted to invest in crypto? Yeah you can by compromised accounts with money in there or by a verified account that wouldn't tie back to you for less than 500 dollars.
Now we'll get into one that I'm sure a lot of you have dealt with in the past. Hacked social media accounts. How many times have you had a friend that just starts suddenly posting the pictures of some miracle before/after weight loss thing, or used watch sale over and over, and maybe even tagging you non stop in it. It's happening to someone I used to know right now on Facebook. The last few weeks he's been posting nonsense and I suspect it's because he hasn't used his account in a while, someone sold the credentials, and now a scam artist is using it to try and get people to click in to the scam. That scam could be malware or it could just be an attempt at stealing money away from anyone that will check it out. As for me, I just blocked them. I could buy a hacked Facebook account online for less than 50 dollars. If I was a twitch streamer? I could buy 1,000 followers for 4 dollars. Just for 4 dollars. You can buy SoundCloud plays, and Instagram followers and spottily listens.
The drawback there and the reason it's so cheap though, is that those kinds of bot activity or social media abuse are fairly easily identified by the actual site and don't often result in actually helping people.
Now let's get into some really illegal stuff you could buy. You can buy forged utility bills or drivers licenses. One interesting thing I see is a you can buy either a New York or Minnesota license, or maybe go across the sea to a Russian passport. Those ones, if you buy just a scanned version are all less than 2,000 dollars.
For actual printed copies, you're looking at anywhere from 150 dollars to 4,000 dollars depending on where it's from.
The last thing I'll cover is something we've talked here before. I don't want to just keep reading off a list so let's talk about the malware and cybercrime goings on.
Say I was jealous of a competitors website and I wanted to, maybe not navigate people to me but navigate people away from them. I could, for 500 dollars, hire a cybercriminal that operates on the principle of cyber crime as a service, often referred to as CSaaS, to flood their website with between 10 and 50k request PER SECOND ….. FOR A WEEK. If I wanted it to go for a month it would only be 850 dollars! This kind of attack, honestly is probably better suited to attacking small businesses that can't afford the kind of protection that would mitigate that stuff, but it's still crazy to think about.
Remember in episode 23 when I talked about distributed denial of service attacks, and people using botnets to use them? This is that kind of thing. You could buy out those tools to try and put a damper on your competition or even just someone you don't like. Remember that analogy of trying to give a speech in an auditorium? Well what if it was a full on stadium that was full and EVERYONE was shouting at you. Not a fun time at all.
In terms of cyber exploits, there's no shortage of different malware and espionage for sale. We've talked about ransomware as a service before and this is definitely where you'd find it. Just last year, the US sanctioned a dark web site named the Hydra Market that specialized in these kinds of deals. It operated as a cybercrime sales broker and cryptocurrency exchanger for threat actors from around the world. It's like the worst version of craigslist you can imagine. Hydra isn't the only place you can buy these services there's a myriad of darkweb sites offering more than just DDOS attacks.
Now, I'm gonna take you back down our own timeline back to episode 1. Remember the colonial pipeline hack? A tool called Darkside Ransomware took down the pipeline and caused an uproar across the country. The custom ransomware was bought on the dark web for just $1262 USD. So based on what we've talked about so far I want to put you in the shoes of a hacker.
You're the cyber menace here and you've got maybe 3,000 dollars in bitcoin. If you wanted to try and turn a profit based on what we've talked about so far you could buy a crytpo account with no ties to you, buy valid credentials to somewhere, and buy custom ransomware all with money left over for you to crack a cold beer and wait for your profits to start coming in.
And this isn't me saying "Hey buddy, let's go do crime" it's me showing you how shockingly easy it is to just buy these services. That's not to say they're guaranteed to get what you pay for, these are criminals after all, but on the flip side all they have is their reputation.
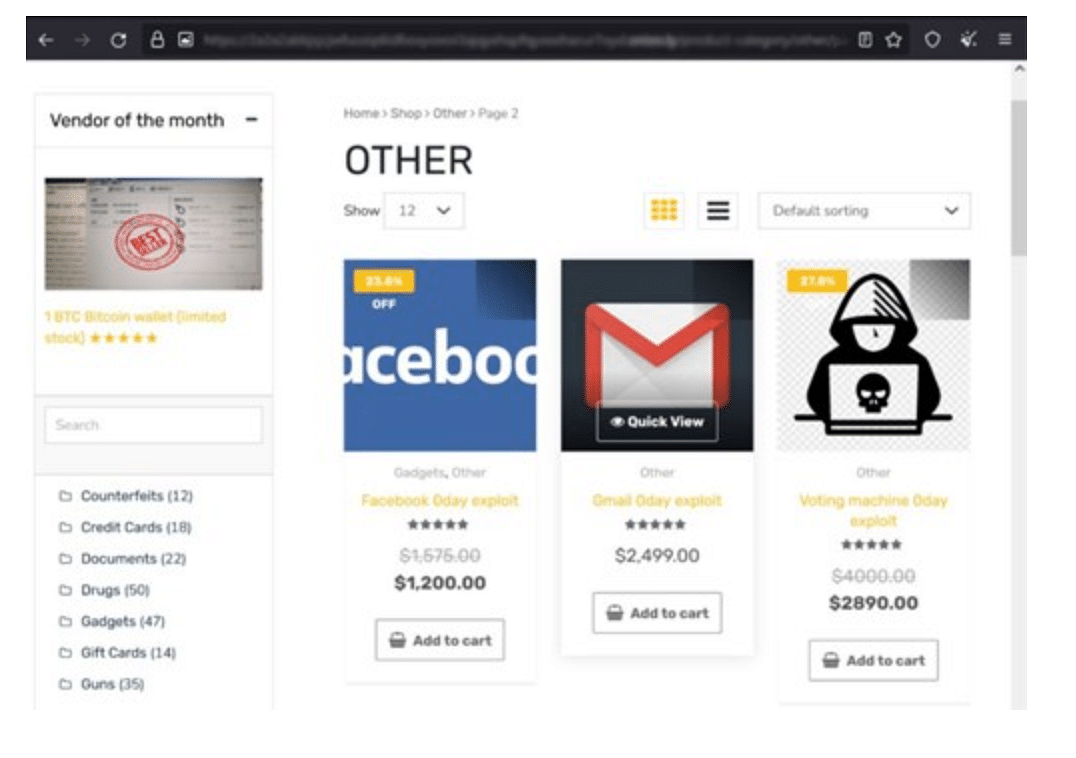
There has been some even bigger stuff to come from dark web sales though. And a shocking look at it too. Let's talk a little bit about Empire Market. Empire market is a pretty interesting case here because if you were to glance at their site, it would look like any other shopping site you'd use. And again, I've got screenshots for you to look on the site and social media.
When you look closer you start to see the filters though that say "Counterfeits", "Drugs", "Gadgets", and Other. And earlier in 2022, if you looked in other you'd see three different zero day exploits for sale. Remember, zero day exploits aren't known to the vendor until they're reported so these are big.
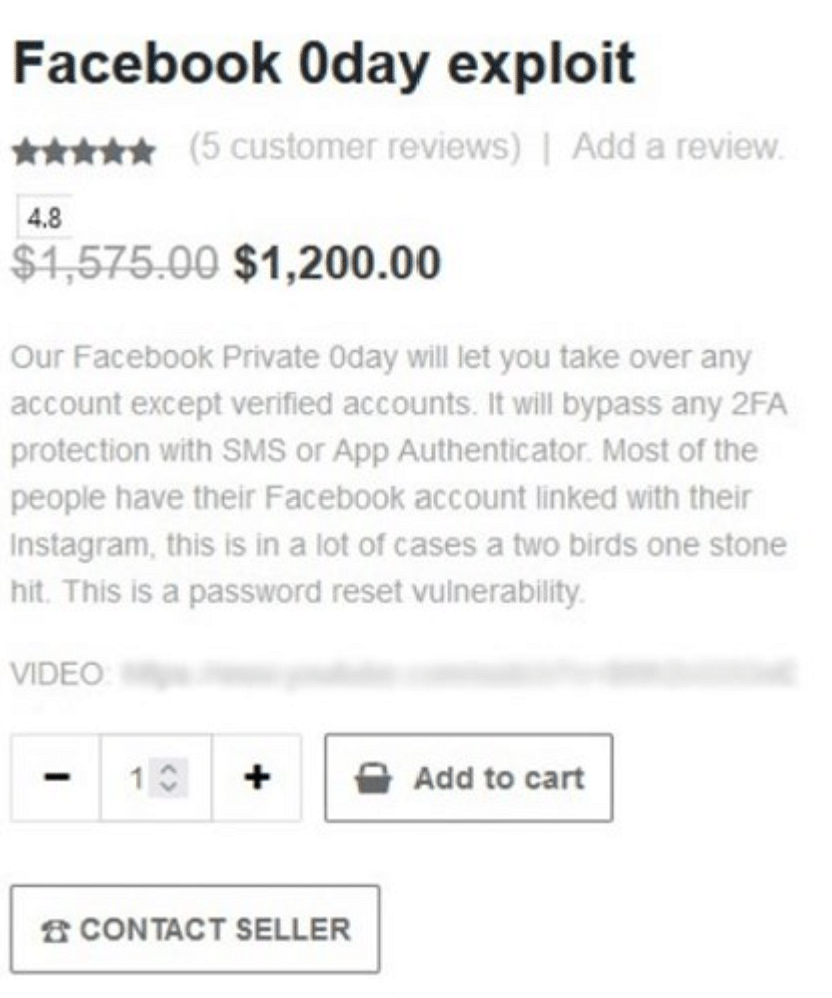
For $1,200 dollars you can get a Facebook zero day that claims to "let you take over any account except verified ones, and that it will bypass 2fa"
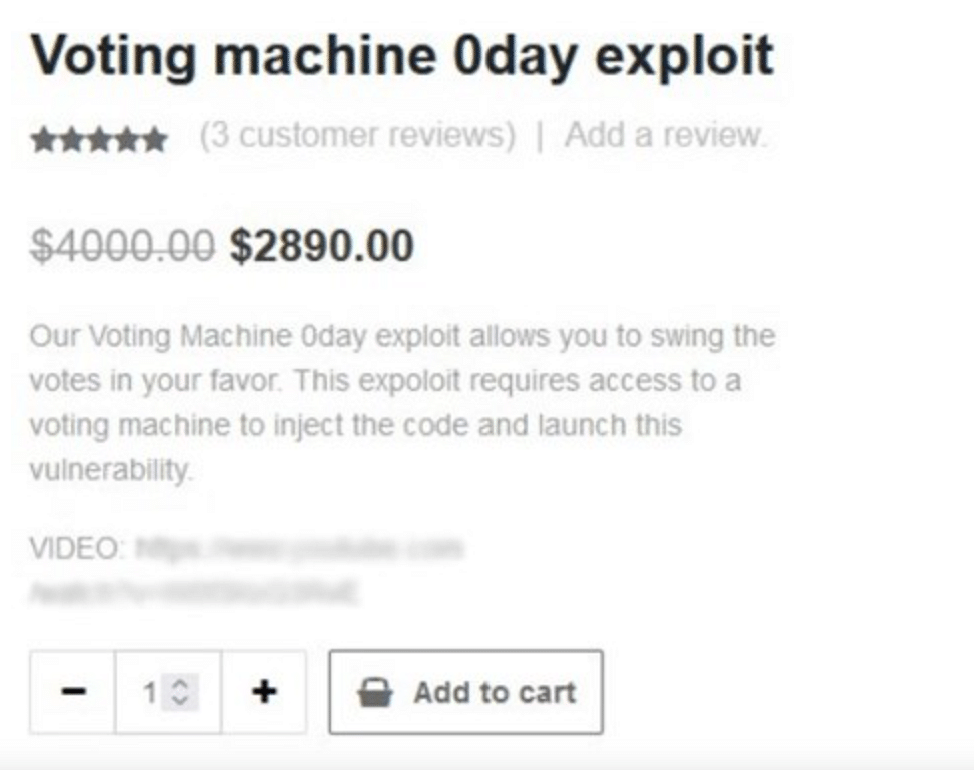
For almost 3k you can get a voting machine exploit that lets you swing votes in your favor if you have access to the machine. A little harder because of how it needs to be delivered but still a major impact.
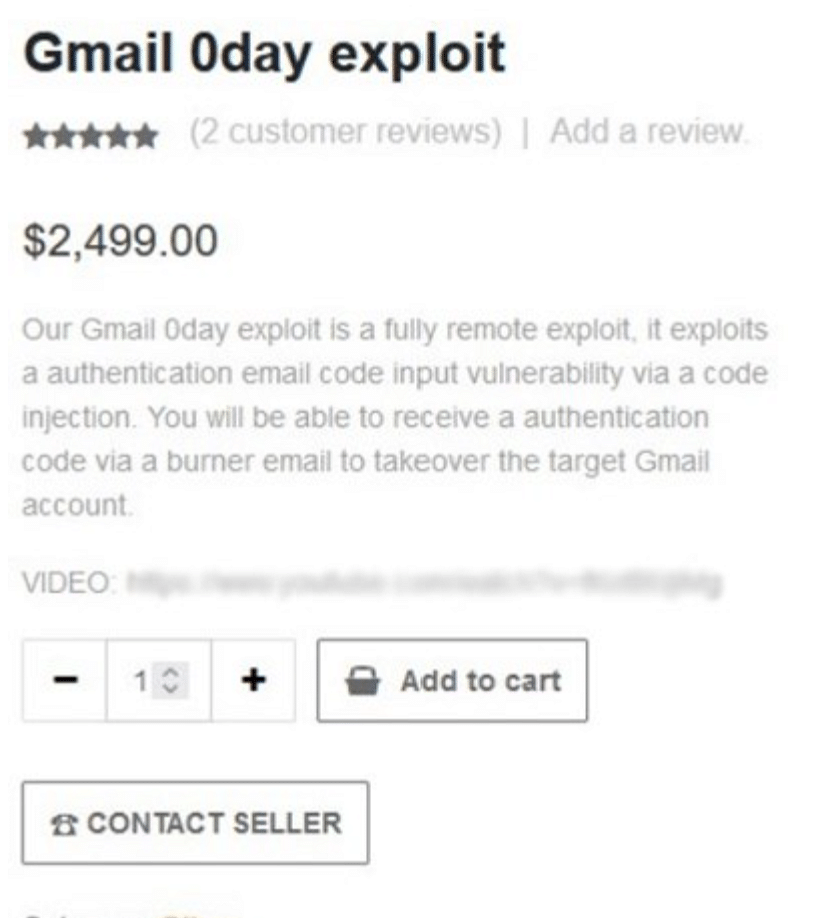
Lastly there was a gmail zeroday that promised full account takeovers with the use of a burner account.
Beneath each of these is an add to car, a customer review section, and a rating in stars! Honestly this has a better UI than some online stores I've used!
It goes back a bit to last episode when I said that crime does pay. The biggest competition for bug bounty hunters can sometimes be the unethical bug hunters that post to these sites and take the anonymous payday.
And remember how we said that Apple pays out big for it's zero days? The last exploit I'll bring up is the one from August of 2022 that allowed attackers to attack the webkit in iOS 15.6.1. This is very rare but there's actual screenshots of a user on a dark web forum selling this for 2.5 million euros. It's hard to compete with that level of cash and the post itself even touts that it's fine to develop these exploits and sell to governments for surveillance. So we know there's not much hangup with how it's used.
That's all to say that the dark web is the biggest cybercrime market to ever exist. In fact, Did you know that if dark web cyber crime was treated as it's own economy on par with other countries, it would be the third largest in the world? According to graphus, the number is about 6 trillion dollars annually placing it just behind the US and China. It's no small thing, and it's growing annually.
We do have a history of taking down some of the sites that tend to appear on the dark web and leave ripples. You've likely heard of silk road before, but if not, the long story short of it is that it was the premiere dark web drug trading site. You could buy cocaine, steroids, the crystal meth, and even Devil's breath. That last one? It's sometimes called the worlds scariest drug. According to complex it allegedly quote "puts users in a hallucinogenic state, but the scary part is that users lose their "free will," so to speak, in that while they're under the influence, they'll do anything that they are told.". So yeah kind of scary stuff. But this site was seized and shut down. It lasted a few years but in October of 2013, the FBI in cooperation with Europol shutdown silk road and arrested the site owner Ross Ulbricht. How long did it take for the next iteration to pop up? Less than a month, luckily that too would shut down.
Ultimately it seemed like a game of bad whack-a-mole. It's insanely hard to find and attribute dark net sites to actionable seizures and arrests. Many times when these things happens it can be not because of what the person did on the dark web but because they slipped up in their day to day life and somehow left a little nugget of a trail back to the site.
There is another part of the dark web that I didn't bring up here and that's got more to do with sex trafficking and exploitation of minors. The reason I'm not bringing this up is because I'm going to tell you it's there, it happens and it's terrible. But frankly I don't think it belongs here in this episode. If I ever do it, it will be a hard episode to write and it will deserve to be told as it's own story with better coverage than as a foot note to this episode. There are deplorable people out there making a profit on the exploitation of others against their will, and I can't begin to describe how that makes me feel even in this small section. Instead I'd like to offer you the opportunity to listen to something else that does do a good job with it. There's an episode of Darknet Diaries called "Welcome to Video" and it details the investigation into one of these sites, the whole process of how a major series of investigations of crypto transfers led to a waterfall of arrests relating to child pornography. From federal agents, to school principals, and south Korean citizens, the story was insane. That episode does the topic the attention it deserves, so I'd recommend going to listen to that.
At this point in the rabbit hole I think I'm ready to call the episode. What I wanted to do with this one was shine a bit of light on the actual topic of the dark web. I wanted you to know that it's not always some scary place and it's not some thing that has no face. It doesn't take an evil genius to use, which is both a bit freeing to know and scary at the same time. But ultimately, it's there and things are happening on it beneath the surface of what we do every day. I'm not going to site here and say you'd be wrong to be a bit afraid of it, but now I hope you at least understand it. I'm John Kordis and thanks for coming on this dive to the bottom of the ocean that is the web.
That's this weeks episode, thanks for listening.
Now before we go, I did promise last episode that there would be a giveaway. If you remember I said that if you reached out to me on social media or in the discord with your guess as to when the first modern bug bounty occurred and got either the first or second major incident year right, I'd enter you in to get a sticker pack. You'll get 2 of each kind of sticker. Well, I decided why not give people a better chance. I'm about to draw for 2 giveaways. First, I'll draw from the people that got it right. When that's done I'm going to draw again twice for everyone but the first two winners. I've had such a great turnout from you all on this that I felt like I should do more than one here so I picked up a few extra stickers. So let's get into it.
I'm happy to say that our three winners are
Adam VV
Mighty Greg Doge
Bearded shrimp
I'll be reaching out to you separately for sending this stuff out, but congratulations!
If you're wondering what that's all about or you're new to the show and might now know about this, you can join us in the discord to talk about the show and hang out! Now that we've started back up I'm going to try and be a bit more active there so you can reach out, talk to me or anyone else online and offer up any suggestions you might have for the show because I'd love to hear them. You can find the link to join on my website whattheshellpod.com or in the description below. On that site you'll also find the transcript of the episode and should you be interested my other socials like Instagram and twitter both of which are @shell_pod.
And then I do want to ask that if you liked this episode maybe leave a review or rating on your platform of choice. It goes a little bit of a ways in terms of getting me up there in the charts so other people can find the show. If that's not your thing maybe just recommend your favorite episode to someone you think might like it, word of mouth is honestly my favorite way the show has spread. Alright, I think I'm good for now, so I'll see you all later when we put out the next episode of "What the Shell?".